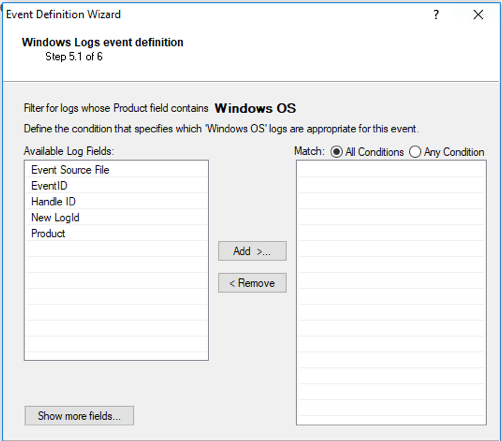
Hik-Connect - Hikvision NVR using Hik-Connect - alarming for "illegal login" attempts | IP CCTV Forum for IP Video, network cameras & CCTV software
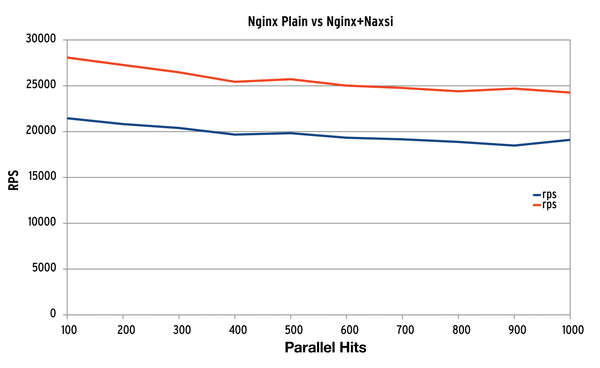
![PDF] Cybersecurity and Network Forensics: Analysis of Malicious Traffic towards a Honeynet with Deep Packet Inspection | Semantic Scholar PDF] Cybersecurity and Network Forensics: Analysis of Malicious Traffic towards a Honeynet with Deep Packet Inspection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/860a4998e2a25d732db28f84f6d503bfc6e1f00c/22-Table9-1.png)
PDF] Cybersecurity and Network Forensics: Analysis of Malicious Traffic towards a Honeynet with Deep Packet Inspection | Semantic Scholar


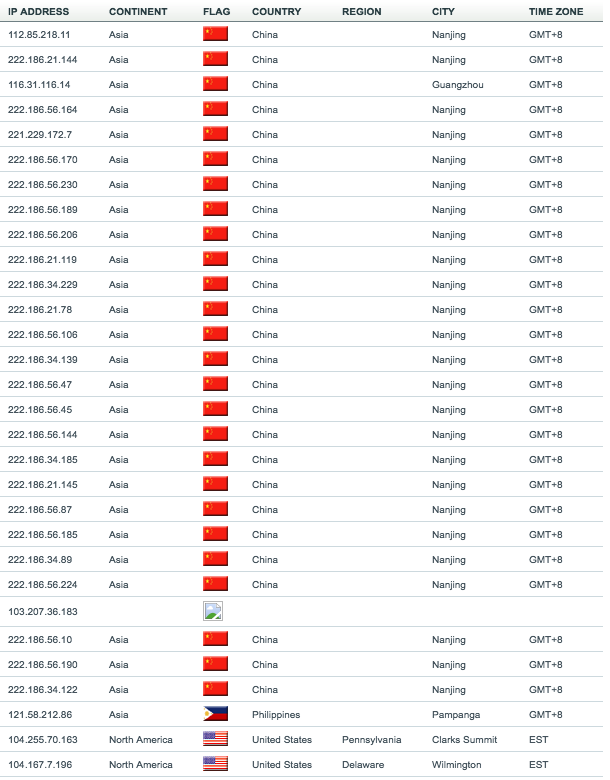
![PDF] Smoke Detector: Cross-Product Intrusion Detection With Weak Indicators | Semantic Scholar PDF] Smoke Detector: Cross-Product Intrusion Detection With Weak Indicators | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/487b881eacb8b9b30b67899ae90780ae293d04cf/3-Figure2-1.png)